Password Recovery on Windows XP
The purpose of this article is to show you, step by step, how to break into a Windows XP machine for which you do not have a valid username and password. There are two intended audiences for this article. The first are people, who for legitimate reasons, have lost of forgotten their username and password and therefore cannot log into their own machine. The other audience are those interested in computer security. For this later audience this article is intended to demonstrate the vital importance of physical security. That is, to show that with physical access, an intruder can break into a Windows XP machine even if that machine is configured to require a username and password to log on.
There are two basic approaches to gaining access to the target machine. The first is to find and decrypt the existing account names and passwords on the system. The second is to actually overwrite the administrator password (usually with a blank one). The second approach is more useful if you have corrupted your system somehow so that the administrator password doesn't work any more. Utilizing the second method carries with it a chance that you could destroy your password hashes (meaning no account will be able to access the machine). This fact, combined with the fact that changing the administrator password is quickly noticeable, renders this second approach a last ditch effort for most cases.
Because Windows XP passwords are encrypted in a unique fashion many password crackers utilize rainbow tables to decrypt them. A rainbow table is a huge list of hashes produced by encrypting passwords. XP passwords are stored encrypted, so your password is actually stored as an encrypted string. A rainbow table is basically a huge index of encrypted passwords and their unencrypted version. By taking an encrypted password and comparing it to these tables you can quickly look up what the unencrypted version of the password actually is. This attack method is successful mainly because creating the rainbow tables is time consuming, but looking up an encrypted password is not. Thus, an attacker can create the tables beforehand, taking as much time as they want, and then crack passwords quickly with the lookup. Of course, the larger the range of options (letter, numbers, symbols, etc.) the larger the table.
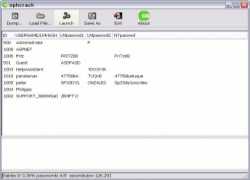
Ophcrack is a quick and dirty cracking tool for recovering Windows passwords. The program itself uses rainbow tables to recover passwords for accounts on a windows machine. The easiest way to use Ophcrack is actually to download and burn the bootable ISO image. This is sort of like a Knoppix distribution (a bootable linux CD) that automatically fires up Ophcrack and begins work on Windows passwords it finds on the host system. Depending on your system setup Ophcrack can save you a lot of time. I found Ophcrack discovered the administrator password on my XP Pro laptop in less than a minute after the boot process completed. Some accounts may take much more time to crack than others. However, if you need access to a machine and you're willing to wait around while Ophcrack does it work then this might be your best bet. I should also note that Ophcrack is not 100 percent reliable. Although it cracked the administrator account on my machine quite quickly it didn't successfully crack a password for one of the user accounts that utilizes special characters. This is a weakness in the included tables, however, not in Ophcrack itself. Because the live CD only includes alphanumeric rainbow tables it won't be able to crack accounts that have special characters in their passwords.
Resetting the administrator password is a little more complex, but relies on the same sort of tools. The first thing you'll need is another Linux boot CD, specifically Knoppix-STD. This is a single, security oriented boot CD packed with useful tools for diagnostics, testing, and security related purposes. What you'll have to do is boot off the Knoppix CD, mount the Windows drives, then use command line utilities to reset account passwords.
The reason this process isn't so straightforward is that the windows passwords are encrypted using information stored in the SYSTEM file, and the hashes themselves are stored in a SAM file. The password hashes are created using registry data, which is stored in several 'hives.' Once all these pieces are located you can monkey with the user accounts fairly easily.
The program you need to use in Knoppix-STD is chntpw. This is a command line utility, so you'll have to open a terminal window to begin. Once the terminal is open you're going to want to mount the windows filesystem. To figure out which is the windows filesystem issue the command:
cat /etc/fstab
look for the entry that reads ntfs after the drive readings. This is the Windows XP drive. Next you'll want to actually mount the filesystem using:
mount -o rw /dev/hda1 /mnt/windows
Assuming that '/dev/hda1' is the drive on which windows is installed. The '/mnt/windows' is arbitrary and you could use any name that you wanted (instead of windows, the /mnt part is actually a specific directory).
Next you'll want to navigate to the directory where the password files are located using:
cd /mnt/windows/WINDOWS/system32/config
This is the directory on windows where the SAM and system file are located (usually C:\WINDOWS\system32\config). Now that you're in the proper directory you can change the administrator password using:
chntpw -u administrator SAM system SECURITY
At the prompt that asks you if you wish to disable SYSKEY select no, at the prompt to enter a new password simply hit return to set a blank password (this is the safest option). Make sure to confirm the change and write the hive files when prompted. This will reset the administrator password to a blank password so you can reboot and log in as the administrator.
Another option is to use Offline NT Password and Registry Editor which is another bootable linux distribution with all the tools you'll need to reset your passwords. This set of tools actually utilizes the same ntchpw program and other utilities as Knoppix-STD, but you may have more success with one tool or the other. For instance, some people report having trouble booting their machine using the Knoppix-STD CD. The nice thing about this utility is that it's pretty straightforward. You simply boot off the CD and answer the questions as they're asked, there isn't any extraneous utility or options on the disk.
Assuming you actually have access to the machine through another legitimate account cracking the passwords for other system accounts becomes much easier. Programs like SAMInside, John the Ripper, PWDump, MD5Crack. Of course, using one of the above methods you could reset or discover the password to a legitimate account, then use that information to log in and utilize these programs. Using cracking tools from the machine itself presents some advantage, but also some challenge. Anti virus or other security protections loaded on the machine might thwart attempts to load such software or crack the password, and without access to the administrator account it might be impossible to disable these safeguards.