Setting Up Public Key Access using PuTTY
Public keys are a great way to log into a remote machine without having to provide a password. This diminishes your security posture somewhat, but done right this can be mitigated. Using public keys allows you to leverage secure protocols like SSH in scripts and automation. Because the public key means there is no password challenge response, scripts can log in and out of remote hosts without human interaction.
The crux of PKA or Public Key Authentication comes down to a pair of keys that are used for verification. RSA key pairs are used. The remote host will utilize a public key to verify that the machine attempting to authenticate holds the corresponding private key. This means that you *must* keep your private key safe (as with any RSA key pair system).
This process begins with the client generating a public/private RSA key pair. The client then exports the public key to the server. The server then needs to be configured to utilize PKA, if it is not already. Once the server is configured it will challenge any connection attempt by asking for the machine to verify the public key. Only the client with the private key can do this. For further security it is usually wise to limit PKA connections to the server from machines known to hold the private key.
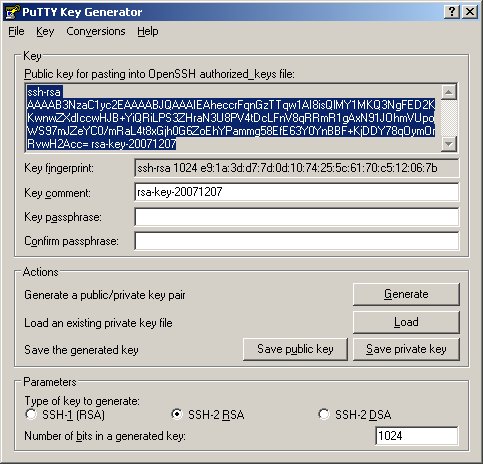
Under Windows this process can be accomplished quite easily using PuTTY. Part of the PuTTY suite of tools available from http://www.chiark.greenend.org.uk/~sgtatham/putty/download.html is the PuTTY Key Generator. This tool can be used to generate RSA key pairs. Once you open up the PuTTY Key Generator, generating the key is fairly straightforward. Click the 'Generate' button and move your mouse around in the blank area of the program window to create 'random' patterns. Once the key generation is complete click the 'Save public key' then 'Save private key' buttons. Be sure to leave the 'passphrase' fields blank. We want to create keys that don't require any pass phrases. Once you have saved the public and private keys to your hard disk you can begin setting up the server.
The first step to setting up the server is to make sure that SSH will accept PKA. Check your sshd_conf file (usually found under /etc/ssh). Look for the lines that govern keys, they should look something like:
PubkeyAuthentication yes AuthorizedKeysFile .ssh/authorized_keys
If these lines are commented out (they have a # symbol at the start) uncomment them by removing the # character. Remember that if you change your sshd_config you'll have to restart ssh to get the changes to take effect. This is usually done with:
[justin]$ sudo /etc/rc.d/init.d/sshd restart Password: Stopping sshd: [ OK ] Starting sshd: [ OK ]
Once SSH is properly configured you need to add your public key to the list of keys known by the server. If you're utilizing the PKA for your own account head to your home directory and look for the .ssh directory. This location is governed by the sshd_config file lines outlined above. If the .ssh directory doesn't exist in your home directory create it. Make sure the directory is world readable (but NOT world writable). Next create a the file authorized_keys in this directory. Be sure the permissions are set similarly to the .ssh directory, so that the file is readable:
[justin]$ ls -lah -rw-r--r-- 1 jukeane jukeane 649 Jul 9 10:21 authorized_keys
Next we have to add the public key to the authorized_key file. On the client machine find the file that PuTTY Key Generator created. It should look something like:
---- BEGIN SSH2 PUBLIC KEY ---- Comment: "rsa-key-20071207" AAAAB3NzaC1yc2EAAAABJQAAAIEAheccrFqnGzTTqw1AI8isQlMY1MKQ3NgFED2K KwnwZXdIccwHJB+YiQRiLPS3ZHraN3U8PV4tDcLFnV8qRRmR1gAxN91JOhmVUpoW S97mJZeYC0/mRaL4t8xGjh0G6ZoEhYPammg58EfE63Y0YnBBF+KjDDY78qOymOrR vwH2Acc= ---- END SSH2 PUBLIC KEY ----
You want tot take the middle portion of that file and add it to your authorized_key file. You can also copy and paste this information out of the PuTTY Key Generator program window to make things easier. Make sure no line breaks show up in your key string. You want to prepend "ssh-rsa " before the key, and add any comments after the key. For instance, the above key in the authorized_key file should look like:
ssh-rsa AAAAB3NzaC1yc2EAAAABJQAAAIEAheccrFqnGzTTqw1AI8isQlMY1MKQ3NgFED2KKwnwZXdIccwHJB+YiQRiLPS3ZHraN3U8PV4tDcLFnV8qRRmR1gAxN91JOhmVUpoWS97mJZeYC0/mRaL4t8xGjh0G6ZoEhYPammg58EfE63Y0YnBBF+KjDDY78qOymOrRvwH2Acc= key for justin
Note that this is all one big long line. Now we want to restrict where this key can be used from. At the start of the line put
from="123.45.67.89"
Replace the IP address with your own (or a DNS name) and be sure to add one space after the IP address, before the "ssh-rsa" part of the listing. Save the file and now we can test it from our client. For our testing purposes we'll attempt to log in using psftp, the PuTTY Secure FTP program:
C:\Program Files\PuTTY>psftp -i C:\ssh_keys\private_key.ppk justin@madirish.net Using username "justin". Remote working directory is /home/justin psftp>
As you can see everything worked properly and I was never challenged to enter a password. This can be used especially well with CVS imports and scripted backups (using tools such as PuTTY SCP). Once enabled you can set up virtually any SSH client to use PKA in order to access this host. This saves an enourmous amount of time, but also means that anyone with access to the host can gain access to the server without any challenge so be wary of where you enable this sort of functionality.