Typical Computer Users Security Guide
This guide is written mainly for the 'typical' or 'home' computer user. I'm writing it to illuminate some common security practices you should follow and some explanations of the various threats you will face whenever you connect your computer to the internet. This article is by no means comprehensive, so if you're serious you should look for further information online.
1. Can you hack into my computer?
Probably not. Home users are relatively safe from remote hacking attempts (someone somewhere else breaking into your computer). The reason for this is that most home computers don't offer any route in. Most computers that get broken into are servers, meaning they work on different operating systems and do things like offer file transfer or web services. Most home computers don't have this capability. Home computers are like houses without doors. Although these houses have windows so that users can look out on the internet, very little makes it back inside your home computer unless you specifically invite it in. The notable exception on Windows home computers are shared directories. Unless you specifically know you need a shared directory you shouldn't have any sharing enabled.

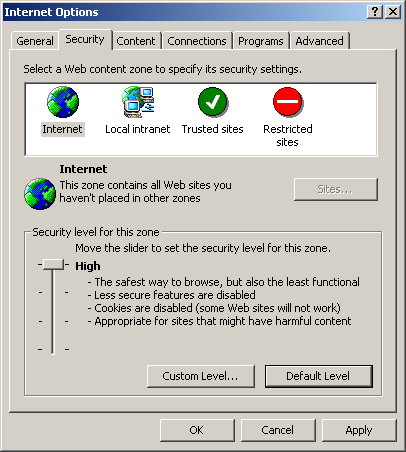
Shares are easy to spot because there is a little hand under the file or folder's icon. Sharing can be enabled and disabled by right clicking the file or folder and choosing 'Sharing' from the pop-up menu. Apples are probably the safest computer to own since not many people have them and their operating system isn't very well understood or usable to most hackers and worm/virus writers. That said, invitation is the surest way to get your home computer hacked. Make sure you don't download anything that you're not sure about. You should set your browser's security level to 'High' to make sure you're less vulnerable. In internet explorer, select 'Tools' from the menu bar, then 'Internet Options...', click the 'Security' tab and set the default level to 'High'. This may be annoying since you will get a lot of pop up confirmations while surfing, but will protect you against to a greater degree.
2. Do I need Anti-Virus software?<
YES!!! All home users should have an up to date anti-virus tool. Make sure to get one that will scan your email as well. Be sure that the software is current and up to date virus definitions are installed. Norton produces an excellent ant-virus software package that automates a lot of its functionality and runs silently in the background. ClamWin is an open source virus scanning tool that is available for free. Make sure to scan your computer at least weekly, schedule the scan if possible for late at night when you won't be using your computer since the scan will bog down your computer and may make it unusable for other purposes while the virus scan is running.
3. Do I need to run Scan Disk a lot?
No, not really. Scandisk or Disk Cleanup isn't understood by most people. All this tool will do is run across your hard drive and reorganize your data for more efficient use by the computer. While it will help performance every once in a while, and will help spot incomplete files, it will not clean up viruses or fix problems with most of your computer. The reason scan disk runs when you improperly shut down your computer is to find operating system files that have been misplaced. When your computer starts up it loads a lot of operating system files into RAM (which is temporary memory enabled by a power supply). If the power is cut these files may not be properly returned to hard disk (permanent storage) and scan disk may help recover some of them.
4. What are macros, do I need them?<
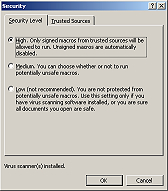
Macros are basically small programs that run inside programs like Outlook or Microsoft Word. Macros are often used by business but hardly ever used by home users. Make sure you 'Disable Macros' (in Word and Outlook click on 'Tools' in the menu bar, then select 'Macros' and 'Security', set these to 'High'). Also make sure to disable the Office Assistant (that annoying paperclip), he can present a security vulnerability. When he appears, right click him, choose 'Office Assistant Options' then uncheck the box next to 'Use Office Assistant' to make him disappear forever.
5. Can I get a virus by surfing the internet?
Yes, follow the steps in #1 above to increase your browser security settings. Make sure they are on high and only download applications from companies and sources you trust.
6. I visited a website and clicked on a link and it showed me my hard drive, have I been hacked?
No, this is a lame trick using a local link. Since web browsers can be used to browse your own computer, all you have to do is put a link in the page that redirects your browser so it is looking at your local computer. This information isn't sent over the internet so only you can see it. Here is an example: Click this link.
7. I visited a website and they knew where I was located, have I been hacked?
No, all the webmaster did was invoke a small program that analyzed your IP address (your IP address is your location on the internet, it is assigned to you by your ISP (internet service provider, such as Verizon or AOL)). Your IP is sent to a website every time you call a page, for instance, right now I know your IP address. IP addresses are assigned to ISPs based on geographic location and thus your IP can be tracked to your access point. If you're in Washington, DC you're access point provided by the ISP is most likely close, so rough geographic information can be plotted using your IP. Check out http://www.networldmap.com/TryIt.htm for more information. To get your IP address open a command prompt (Start -> Programs -> Accessories -or- Start -> Run -> command.exe) and type 'ipconfig'.
8. I keep getting spam, how do people know my email address?
This is sort of a complex problem that mostly arises from people using HTML enable email viewers (such as Outlook). What happens is I send an email to a bunch of addresses that may or may not work. I embed an image into my email and code it in such a way that when you read the email your email viewer requests the image from my server. I then review my server logs and find out which email addresses viewed my email (by tracking image requests). Once I know your email is good (you requested the image) I send you 10 more pieces of spam and sell your address to a bunch of my spammer buddies. The only way to prevent this is to use an email viewer that doesn't use HTML (that pretty much rules out all web based email viewers like Hotmail and Yahoo! Mail), or to get a good personal firewall that will block these outgoing requests (Zone Alarm does a great job of this). Also be sure to never post your email address online (to message boards, newsgroups, etc.).
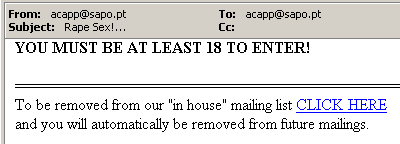
NEVER EVER EVER UNSUBSCRIBE TO A SPAM MESSAGE!!!! All you are doing is confirming your email address to the spammer, and this will ensure you will get even more spam! You may want to get a free account that you use only for posting online. Many online vendors will sell your address as well, so be careful when buying online. Read terms of use, and email policy. Also be sure to never sign up for a mailing list unless you're certain you want the content, you may have trouble unsubscribing.
9. Do I need a personal firewall?
Yes, these days your really do. Personally I use Black Ice, but I have found Zone Alarm and McAffee Personal Firewall and Norton Firewall all to be very good. You will be surprised by the number of hack attempts you receive after you install your firewall. Most of these are just people randomly scanning around the internet, but a firewall will protect you against almost all of them.
10. Who gets hacked most often and why?
Well, servers with static IP addresses get hacked most often because they are always on and always in the same place. Broadband users (cable and dsl) get hacked a lot too since although they don't have static IP addresses they are online for a long time and have fast connections. Dial-up users are at the bottom of the hacking target list since they have slow connections, and their IP address changes every time they dial in.
11. I've got Broadband (DSL/cable), what is the best way to protect myself?
Get a Cable/DSL router with some firewalling options and NAT (network address translation). These machines dial up your connection for you and keep it on. They also protect you with NAT. They get one IP from your ISP and use it to mask all the connections from your home computers. This means that anyone trying to hack your home computers will have a really tough time getting past your router. You may have 12 computers at home, but from the internet it looks like you only have one (the router). Make sure you reset (or set) the default password on your router so it doesn't get broken into. If you have a personal firewall and then install a router, you will notice that your firewall won't log any more hacking attempts :) This is your router doing its job. Be sure to read the documentation that comes with your router. My personal recommendation is the Netgear Cable/DSL Web Safe Router with Content Filtering pictured below:

12. Do I have to do anything else to protect my computer?
Yes! Make sure you update your software and operating system at least once a month. Windows users should use the 'Windows Update'
option in their Start menu or got to http://windowsupdate.microsoft.com and download all the latest patches and security fixes for all your programs as well as your operating system. These patches will protect you from the latest viruses, worms, and security threats to your computer.
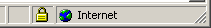
13. Should I be worried about identity theft or my credit card number getting stolen?
Yes, make sure you always use SSL encrypted connections when entering your credit card number online. The little padlock on your browser lets you know your connection is secure. MAKE SURE IT IS THERE!
14. Can my email get hacked?
Yes, quite easily in fact. Make sure you use a good password to protect all your accounts online. Read my diatribe on passwords (link at bottom) to choose a good password. Change your password every so often, and don't use the same password for different accounts. POP3 email is easy to brute force (a password guessing attack) so make sure you change your email password every so often. Also, your email can get intercepted in transit. NEVER SEND A PASSWORD VIA EMAIL!!! If you are worried about email security, download and install PGP. PGP is an encryption program that works really well to secure your email communication and works seamlessly with most email programs.
Related Links: