GnuPG on Windows
Installing GPG
GPG is the GNU Privacy Guard, the free, open source alternative to PGP (Pretty Good Privacy). You can use GPG in all the same ways that you would use PGP - for encryption and digital signatures most commonly. You can use GPG to encrypt your e-mail or files on your filesystem. It's an open source standard so you never have to worry about being locked out of your files or having the program become unavailable. GPG also supports interoperability with PGP so you can use it as a full replacement.
The first step in using GPG is to download and install it. Downloads are available from http://www.gnupg.org/download/. Look under the section labeled 'Binaries' and click on the FTP site for the latest compiled version. At the time of this writing it was gnupg-w32cli-1.4.6.exe. This is the Windows 32 bit Command Line Interpreter version of GNUPG. Don't worry about the command line part, we'll get to installing graphical utilities to help you maintain your installation later.
Once you've downloaded the installer go ahead and double click on it. This should bring up the graphical installation wizard.
Go ahead and follow through the wizard. The default values are acceptable for most users.
Once you're done you'll notice that not much has happened. However, GPG is now installed. You'll notice that in the default file installation path (if didn't change anything during the installation) C:\Program Files\GNU\GnuPG\gpg.exe is now in place.
At this point you can use GPG at the command line. The first thing you'll want to do is set up your key pair. GPG works in exactly the same way as PGP - you need a public and a private key. The private key is the important one, if you ever lose it your encryption is useless. The public key is the 'cypher' that will be used to encrypt messages so that only your private key can decrypt them. GPG uses one-way encryption, meaning that the method used to encrypting the data can't be used to decrypt it.
For instance, there is a fairly simple encryption scheme called ROT-13. In this encryption scheme you move every letter in the alphabet 13 letters further along in the alphabet. So the letter 'a' becomes the letter 'n' in a ROT-13 scheme, and the letter 'b' becomes the letter 'o' and so on. This scheme is not one-way encryption since you can use the encryption method to decrypt a message as well.
GPG uses complex encryption so that the method used to encrypt the message (the public key) cannot be used to decrypt it. Because of this, only the private key can be used to decrypt messages. This means that you can give away your public key to anyone who wants to send you encrypted messages, and they'll never be able to decrypt your messages - even if they were the ones who encrypted them. Of course to make this scheme work you'll have to exchange public keys so the encrypted communication can be two ways.
For now let's work on creating a key pair. This is a public/private key combination that you can use to encrypt your own stuff and the public key you can distribute. This key can also be used as a digital signature.
Digital signatures are crafted by taking the contents of a message, generating a number, then translating that number using your private key to create a 'signature' number. Anyone with your public key can then look at the contents of the message and compare it to the signature using your public key and verify that it was created using your private key. This allows a recipient to verify not only that you sent the message, but also that the message contents were not changed at all.
Generating a Key Pair
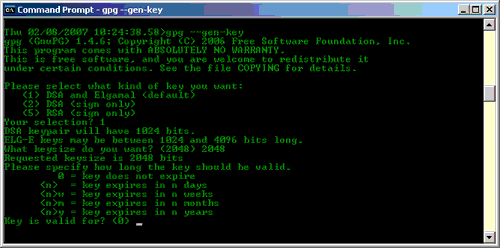
To create your key open up the command prompt (Start -> Run -> 'cmd.exe') and type:
gpg --gen-key
This will lead you through a series of questions. You should answer with the default answers if at all possible.
You can now check to see your key in the key database by typing:
gpg --list-secret-keys
Be sure to use a good passphrase when prompted. If you want to export your key (i.e. get your public key in a file that you can give to someone else) use the syntax:
gpg --output [filename] --armor --export [key uid]
For instance, if when I issue a 'gpg --list-secret-keys' I see:
C:/Documents and Settings/justin/Application Data/gnupg\secring.gpg -------------------------------------------------------------------- sec 1024D/C36BEECE 2007-02-08 uid justin klein keane (this is just a test) <foo@bar.com> ssb 2048g/02A29A7C 2007-02-08
Importing/Exporting Keys and Encrypting Files
To get the public key in a file called justin.pub to export I use:
C:\>gpg --output justin.pub --armor --export justin klein keane
Now you're probably wondering how to encrypt a file? Once you've got a public and private key it's pretty simple. Let's say I have a file in C:\temp\secret.txt and I want to encrypt it. I navigate to the file location and use the gpg --encrypt like so:
C:\> cd C:\temp C:\> gpg -e secret.txt C:\> dir Volume in drive C is SYSTEM Volume Serial Number is 148B-1CF4 Directory of C:\temp 02/07/2007 10:42 PM <DIR> . 02/07/2007 10:42 PM <DIR> .. 02/07/2007 10:41 PM 6 secret.txt 02/07/2007 10:42 PM 606 secret.txt.gpg
And you can see the new secret.txt.gpg file has appeared. This is the encrypted version of the file that only I can decrypt. To decrypt the file I simply use the '-d' flag instead of the '-e' like so:
C:\> gpg -d secret.txt.gpg
And you're done. If you want to encrypt a message to someone else you'll first need to get their public key and import it to your keyring. You can accomplish this using:
C:\> gpg --import new_key.pub
Once you have the key you can encrypt a file so that only the owner of the secret key corresponding to the public key you use to encrypt the file with can decrypt it. For instance, let's say your friend Sam sent you their public key as an e-mail attachment. You saved that attachment to your C drive and imported it using:
C:\> gpg --import sam.pub
Next you want to encrypt the file 'secret.txt' so that only Sam can read it. You'd encrypt the file using the '-r' (recipient) flag after you found the UID for Sam's key using the 'gpg --list-keys' command. Assuming the UID was 'Sam Spade' you'd use:
C:\> gpg -r Sam Spade -e secret.txt
Now you could send Sam the file as an email attachment or put it on a thumb drive or whatnot and be assured that only he could decrypt the file and use it.
Graphical Front Ends
You can quickly observe the versatility of the command line version of GPG, but you're probably already noticing that in a graphical based operating system like Windows this is a bit unwieldy. Wouldn't it be nice to simply right click on files and select 'encrypt' or use a GUI to manage your keys? Well, there are programs that allow you to do all of that. Luckily they're all bundled together in a package called GPG4Win. Using the tools in that package you can easily manage GPG, encrypt and decrypt your files, and utilize GPG using your GUI. There are even tools for using GPG to encrypt your e-mail in Microsoft Outlook 2003.
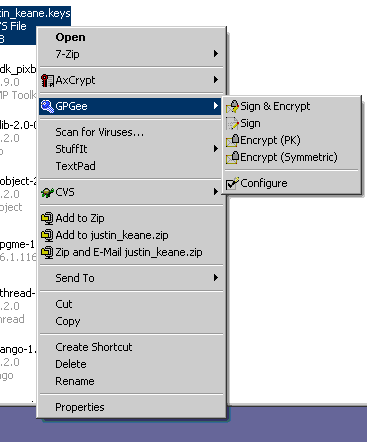
GPG4Win also includes the GPGee package, which allows you to encrypt files on your filesystem just by right clicking on them:
If you plan to use Thunderbird as your e-mail client you only have to download one more package to use GPG encryption with your e-mail. The http://enigmail.mozdev.org/ Enigmail extension allows you to encrypt messages, and even manage your GPG keys through Thunderbird (or Mozilla/Netscape mail).
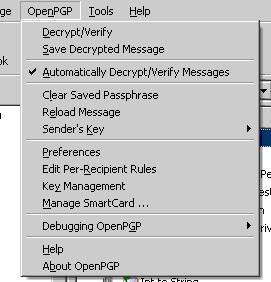
Enigmail will allow you to digitally sign your e-mail as well as encrypt actual e-mail and even any attachments. This is a perfect security enhancement if you have sensitive information that you want to be able to transmit securely via e-mail.
Conclusions
Installing and configuring GPG is relatively straightforward. With a little work you can easily be up and running, utilizing encryption on both your filesystem and for your e-mail. This added security is perfect for protecting sensitive files at rest or in transit. GPG's widespread adoption and ongoing open source community support ensure that it will be a common and fairly ubiquitous solution for some time to come. With data and privacy security on the rise there's no reason not to use a solution as simple as GPG.