Web Bugs in Hot Teen Action!
What is a Web Bug?
At its core, all a web bug consists of is an image. Usually these images are one pixel by one pixel transparent GIF images, although the format isn't very important. Web bugs are used to track usage by exploiting the way in which HTML image rendering works. Web bugs are found most commonly in email but can also be used on web sites to track usage.
Common Usage
Web bugs are most often found in spam email messages. The reason for this inclusion is to track which spam recipients view what spam messages. Bulk emailers (including legitimate marketers) could keep a large database of addresses, but the addresses may or may not actually lead to a real inbox. The bulk emailer can use a web bug to determine if the message is actually opened and read.
The key to this equation is utilizing HTML based email. Sending actual images embedded in email makes the email very large and cumbersome. Such messages take a long time to deliver and consume bandwidth. As an alternative, many email composers will use HTML and merely reference images hosted on remote servers. Because many email clients are HTML compliant they will compose messages by pulling down images included in email, even if those images reside on remote servers.
Web servers keep detailed logs about what requests come in and out. These logs will also record requests for images. So if you view a web page, the web server logs will include requests for the actual page text, along with requests for any images that are included. By including an image link in an email you can trigger an email client to request the image, and thus the server can generate a log that includes the date, time, IP address and name of the image requested.
Composing an HTML based email message you can easily embed specially crafted image links that point back to a server you control.
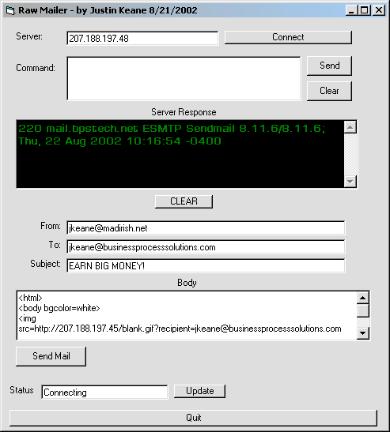
By crafting an email message, for instance, that included the following text:
<html> <body bgcolor=white> <img src=http://207.188.197.45/blank.gif?recipient=your@email.com border=0> Earn big money while I spy on you! </body> </html>
a bulk emailer could include a tiny image (in this case called "blank.gif") in the email message. You'll also notice that the image request contains options arguments (the material after the "?") that will also be logged along with the image request. In the above case the resultant email would look relatively benign in an Outlook email client:
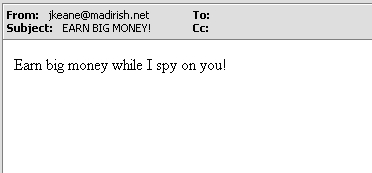
As you can see the web bug is completely invisible to the end recipient. However, as soon as the email is opened and composed by Outlook the following web log entry is created on the machine that hosts the image:
207.188.197.45 - - [22/Aug/2002:13:38:26 -0400] "GET /blank.gif?recipient=your@email.com HTTP/1.1" 200 43
The first entry is the IP address of the email recipient, then the date and time, then the request method (in this case GET) then the actual page requested (or in this case image), and the response codes (200 for OK). You can see that the email address that was tacked on to the end of the image specification is included in the web logs. Bulk emailers utilize programs that automate the composition of these emails so that each email is tagged with a unique identifier specific to the recipient. In the above example we have been fairly obvious, but often bulk email will include a much more innocuous string to disguise the intention of the web bug. For instance, the bulk emailer could keep a table that maps the string 'adakljdflkajkljj23434' to the email address 'jkeane@somewhere.com' and so the web bug code would actually look something more like:
<img src="http://207.188.197.45/header.gif?p=adakljdflkajkljj23434"/>
As you can see this email source code doesn't reveal that the email actually is serving to identify the recipient. Furthermore, the web bug itself doesn't have to necessarily be invisible or a tiny image. An emailer could tag an image that is included in the body of the message for display. For instance, a logo or a picture that is in the email could be "bugged" with such a tag. Often times legitimate email senders will do this to track the effectiveness of email campaigns (to determine how many people received a specific marketing email for instance). Once the messages are sent out the mailer simply parses through their web logs, correlating the bugs with specific email addresses in order to determine how good their mailing list is (in terms of how many people viewed their message) as well as determining email reading habits of their targets.
Protecting Yourself
While web bugs may seem sort of annoying, they're also invasive. The fact that email senders can passively collect information about your email reading habits is a threat to your privacy. While this isn't a grave issue, it can be used as part of a greater campaign to whittle away your anonymity online. In addition to exposing your email address as a "live" one, you are also providing feedback to marketers without your consent.
Unfortunately the only way to protect yourself for now is to disable images from being displayed within your email. The safest thing to do is to utilize a text based email client. This does, however, detract from the overall attractiveness of email, and many marketers don't even provide text versions of their email. For instance, many companies will send emails to their customers that consist solely of an image that contains the marketing information. This forces the viewer to display the image in order to receive the message (and thus, unwittingly giving away information to the marketers).
It would be nice to have an email client plug in that would be able to scrub the additional arguments from image strings, but even this could be end run technically. Ultimately any time you read an email message that includes remotely hosted images the reader must compromise certain aspects of their privacy and anonymity in order to view the imagery.
Conclusions
If you must read email with images included be selective about what emails you read. Messages that are obvious spam should be deleted before they are viewed. Remember, even if an email is displayed in a 'preview' pane, if any composition of the message body is done there is potential for a web bug to report the activity. For this reason it is imperative that the email be deleted before any display is done by your email client.
Related Links
- The Web Bug FAQ The EFF (Electronic Freedom Foundation) has an excellent write up of web bugs and how they are used.
- Privacy basics - Thunderbird Thunderbird, Mozilla's free, open source email client has robust privacy features that include blocking remote images.
- EPIC The Electronic Privacy Information Center has logs of useful tools, links and articles about protecting your electronic privacy.